Cybersecurity isn’t slowing down. Actually, it’s accelerating faster than most organizations can handle. Every 39 seconds, there’s a cyber attack happening somewhere in the world. And guess who’s standing between chaos and security? SOC Analysts.
If you’ve been wondering whether SOC analyst training is your gateway into cybersecurity, you’re asking the right question. Because here’s the thing companies aren’t just hiring anymore. They’re desperately searching for trained professionals who can actually do the work, not just talk about it.
That’s where proper SOC analyst training with hands-on labs becomes your competitive advantage.
What Is SOC Analyst Training?
Let’s cut through the noise.
SOC analyst training isn’t another generic cybersecurity course that dumps theory on you and calls it a day. It’s a structured, job-oriented program specifically designed to prepare you for real Security Operations Center environments where actual threats are detected, analyzed, and neutralized.
Think of it this way. You wouldn’t send someone into a surgery room after just reading medical books, right? Same logic applies here.
At Go Hackers Cloud, we’ve built our SOC analyst training program around one core principle: if you can’t do it in a lab, you won’t survive in production. That’s why we’ve designed hands-on environments using enterprise-grade SIEM tools, live attack simulations, and real-world incident response scenarios.
We’re not teaching you about SOC work. We’re training you to be a SOC analyst from day one.
Our curriculum covers everything from threat detection workflows to security alert triage, log analysis, and incident documentation exactly what you’ll face in industries like finance, healthcare, SaaS, and government sectors.
Why Choose SOC Analyst as a Career in Cybersecurity
Here’s something most training providers won’t tell you upfront.
Not all cybersecurity roles are created equal. Some require years of prerequisite experience. Others demand advanced coding skills or deep system architecture knowledge. But SOC analyst course roles? They’re different.
SOC Analyst positions are genuinely entry-level friendly while offering serious career growth potential. You can start as an L1 analyst monitoring alerts and escalate to L3 roles doing advanced threat hunting within a few years.
Why this career path makes sense:
The demand is relentless. Cyberattacks increased by over 38% in recent years, and every breach creates more SOC job openings. Companies need trained professionals immediately.
The career trajectory is clear. Unlike vague “cybersecurity roles,” SOC has defined levels L1, L2, L3 each with specific responsibilities and salary jumps. You know exactly where you’re going.
The skills are transferable. SIEM knowledge, log analysis, incident response these capabilities open doors to threat intelligence, incident response management, and even security architecture roles later.
Job stability is real. Even during economic downturns, security operations continue. Actually, they intensify because attacks don’t pause during recessions.
And honestly? There’s something satisfying about being the person who catches threats before they become headlines.
Who Should Enroll in SOC Analyst Training
We’ve trained everyone from complete beginners to seasoned IT professionals making career pivots.
Our SOC analyst training for beginners works because we don’t assume prior knowledge. If you’re starting from scratch, we’ll build your foundation properly networking basics, operating systems, security fundamentals before diving into SOC-specific skills.
This training is designed for:
Fresh graduates who want job-ready skills instead of just certificates. You’ve got the degree, now you need the practical experience that employers actually test in interviews.
IT professionals transitioning into security. Maybe you’ve been in helpdesk, network administration, or system support and you’re ready to level up into a specialized security role.
Working professionals seeking career growth. You can’t leave your current job but you want to skill up for better opportunities. Our flexible learning modes support that.
Career changers entering cybersecurity. You’ve decided tech security is your path but you need structured guidance and mentorship to break in successfully.
Network and system administrators upskilling into SOC. You understand infrastructure already now you’re adding the security operations layer that dramatically increases your market value.
The SOC analyst course online format means location doesn’t matter. Lab access doesn’t expire at 5 PM. You practice when it works for your schedule.

SOC Analyst Roles & Responsibilities (L1, L2, L3)
Understanding the role levels matters because it shapes your learning path and career expectations.
SOC Analyst L1 – Monitoring & Triage
This is where most people start. And honestly, it’s more challenging than it sounds.
You’re monitoring security alerts across multiple tools. Your job is identifying what’s real versus what’s noise. False positives can overwhelm a SOC, so your triage skills determine whether critical incidents get the attention they need.
You’ll document everything. Every alert reviewed, every decision made, every escalation triggered. This documentation becomes crucial for L2 analysts and compliance audits.
Escalation is an art. Knowing when to escalate and how to communicate findings clearly separates good L1 analysts from great ones.
SOC Analyst L2 – Investigation & Analysis
Now you’re diving deeper.
Deep log analysis becomes your daily work. You’re correlating events across systems, tracing attack paths, identifying compromised accounts or systems.
Malware analysis and phishing investigations land on your desk. You determine if that suspicious file is actually ransomware or if that email campaign successfully compromised user credentials.
Containment actions fall under your responsibility. You’re coordinating with IT teams to isolate infected systems, block malicious IPs, or disable compromised accounts before damage spreads.
SOC Analyst L3 – Threat Hunting & Response
This is where things get interesting.
Advanced threat detection means you’re not waiting for alerts. You’re actively hunting for indicators of compromise that automated tools might miss.
Incident response coordination puts you in charge during major security events. You’re directing the response, communicating with stakeholders, and ensuring proper remediation.
SOC process optimization becomes part of your role. You’re improving detection rules, reducing false positives, and mentoring junior analysts.
Our SOC analyst training program prepares you for all three levels, so you’re not just ready for your first job you’re ready for your entire career trajectory.
Skills You Will Gain from SOC Analyst Training
Theory without application is worthless in cybersecurity.
That’s why our SOC analyst certification training focuses on hands-on skill development that employers actually test during interviews and probation periods.
Core technical skills you’ll master:
Log analysis and correlation across multiple sources. You’ll learn to read firewall logs, endpoint detection logs, server authentication logs, and network traffic captures then correlate events to identify attack patterns.
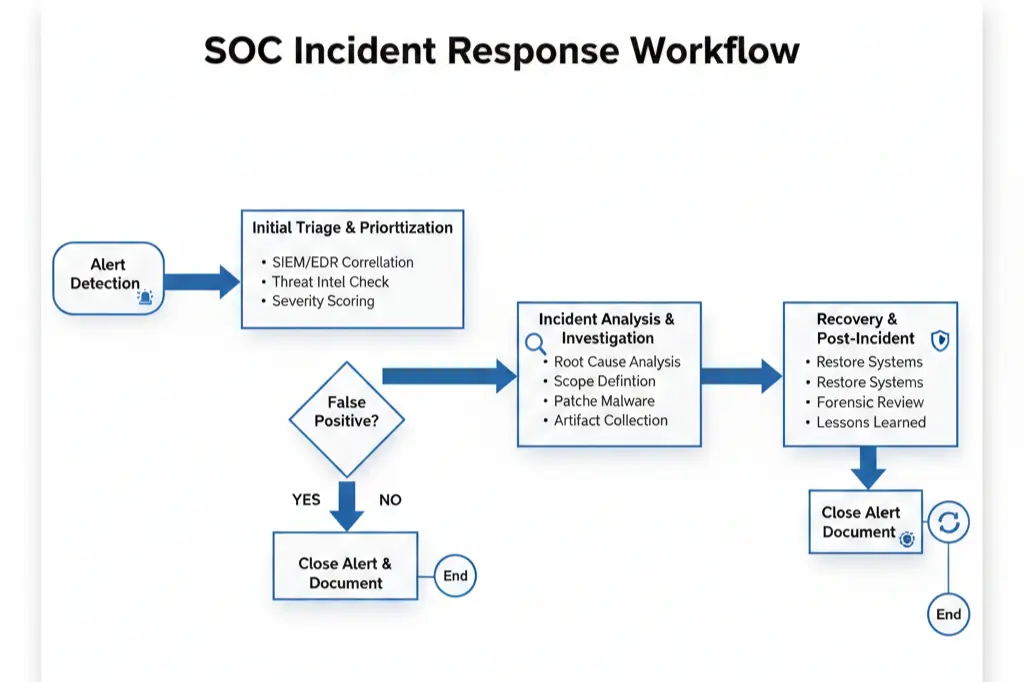
Incident response handling following industry frameworks. NIST, SANS these aren’t just acronyms. You’ll practice actual incident response workflows from detection through containment, eradication, and recovery.
Threat intelligence analysis and application. Raw threat data is useless without context. You’ll learn how to consume threat feeds, identify relevant indicators, and apply intelligence to your organization’s specific environment.
MITRE ATT&CK framework mapping. Understanding attacker tactics and techniques helps you anticipate next moves and improve detection coverage.
Security alert investigation methodologies. Not every alert is created equal. You’ll develop the investigative approach that separates real threats from false positives efficiently.
SOC reporting and documentation standards. Clear communication matters. You’ll practice writing incident reports, shift handover notes, and executive summaries that different audiences can understand.

These aren’t checkbox skills. You’ll apply them repeatedly in lab scenarios until they become second nature.
Tools Covered (SIEM, EDR, SOAR, Threat Intelligence)
Here’s where many training programs fail. They talk about tools instead of letting you actually use them.
Our SOC analyst training with real-time SIEM tools gives you hands-on exposure to the actual platforms and technologies you’ll encounter in production SOC environments.
SIEM Platforms: You’ll work with security information and event management systems that aggregate and analyze security data. Understanding SIEM architecture, search queries, correlation rules, and dashboard creation becomes practical knowledge, not theoretical concepts.
EDR/XDR Tools: Endpoint detection and response platforms are your eyes on individual devices. You’ll practice investigating endpoint alerts, analyzing process trees, and identifying malicious behavior patterns.
SOAR Automation: Security orchestration and automated response platforms are changing how SOC teams operate. You’ll understand automation workflows, playbook development, and when automation enhances (versus replaces) human analysis.
Threat Intelligence Platforms: Raw threat feeds need to be actionable. You’ll work with threat intel platforms to identify relevant indicators, understand threat actor behaviors, and apply intelligence to your detection strategies.
Log Sources: Real SOC work means understanding diverse log sources firewalls, proxies, DNS servers, authentication systems, cloud platforms. You’ll practice extracting security-relevant information from each.
We’ve structured labs around realistic scenarios where you’ll use multiple tools together, just like real SOC operations where insights come from correlating data across platforms.

Hands-On Labs & Real-World Attack Simulations
This is where everything clicks.
Reading about phishing attacks is one thing. Actually investigating a simulated phishing campaign where you need to identify compromised accounts, trace email headers, and recommend containment actions? That’s completely different.
Go Hackers Cloud delivers SOC analyst training with hands-on labs that replicate actual attack scenarios SOC teams face daily.
Attack scenarios you’ll investigate:
Brute-force authentication attacks where you’ll analyze failed login attempts, identify attack sources, determine if any accounts were compromised, and recommend security improvements.
Phishing campaigns requiring email analysis, URL investigation, attachment examination, and user impact assessment.
Malware execution scenarios where you’ll trace initial infection vectors, analyze malware behavior, identify affected systems, and coordinate containment.
Insider threat investigations involving unusual data access patterns, unauthorized file transfers, or policy violations requiring sensitive handling.
Data exfiltration attempts where you’ll identify abnormal network traffic, trace data movement, and determine what information might have been stolen.
Each lab scenario includes the messy reality of SOC work incomplete information, time pressure, and the need to make decisions with imperfect data.
You won’t just get the “right answer” handed to you. You’ll practice the investigative process that builds real analytical skills.
SOC Analyst Training Curriculum Overview
Our curriculum follows a progressive path designed around one goal: getting you job-ready.
Foundation Phase: We start with cybersecurity fundamentals and networking basics. Understanding TCP/IP, DNS, HTTP, and common protocols matters because you’ll analyze this traffic constantly. Linux command-line basics get covered because many security tools run on Linux systems.
SOC Processes & Workflows: You’ll learn how actual SOC teams operate shift structures, escalation procedures, ticketing systems, and communication protocols. Understanding the operational context makes technical skills more effective.
SIEM Deployment & Log Analysis: This is where technical depth increases. You’ll understand SIEM architecture, log collection, parsing, normalization, and search query development. Log analysis becomes practical as you investigate real scenarios.
Incident Response & Case Handling: Following established frameworks, you’ll practice complete incident response workflows from initial detection through containment, eradication, recovery, and post-incident analysis.
Threat Hunting Fundamentals: Moving beyond reactive monitoring, you’ll learn proactive threat hunting techniques, hypothesis development, and hunting methodologies.
Capstone SOC Project: Everything comes together in a comprehensive project where you’ll operate as a SOC analyst handling multiple concurrent security events, prioritizing response, and documenting your work professionally.
This isn’t a linear “watch videos then take a quiz” approach. Each phase includes applied labs where you practice concepts immediately.
Certifications Aligned with SOC Analyst Roles
Certifications validate your skills to employers who can’t assess technical ability from resumes alone.
Our SOC analyst training program aligns with globally recognized certifications that hiring managers actually value.
CompTIA Security+ establishes your foundational security knowledge across various domains. It’s vendor-neutral and widely respected as an entry credential.
Blue Team Level 1 certification focuses specifically on defensive security operations exactly what SOC analyst roles require. It tests practical skills, not just memorization.
SOC Analyst certifications from various providers validate role-specific competencies in security monitoring, incident detection, and response.
Vendor-neutral SOC skill frameworks ensure you’re learning transferable capabilities rather than tool-specific tricks that become outdated.
We provide certification guidance as part of the training roadmap. But here’s the reality certifications open doors, but practical skills keep them open. That’s why we emphasize hands-on capability development alongside certification preparation.

Career Opportunities & Salary After SOC Training
Let’s talk about what actually happens after training.
Completing SOC analyst training with placement support prepares you for multiple role pathways depending on your background and interests.
Common entry roles:
SOC Analyst L1/L2 positions at companies running 24/7 security operations. You’ll monitor threats, investigate alerts, and respond to incidents as part of a larger team.
Cybersecurity Analyst roles that might blend SOC responsibilities with other security functions like vulnerability management or compliance.
Threat Monitoring Analyst positions focused specifically on threat detection and alert triage in organizations with specialized security teams.
Incident Response Analyst roles emphasizing investigation and remediation rather than ongoing monitoring.
Salary expectations (realistic numbers):
Entry-level positions in India typically range from ₹4-7 lakhs annually. That’s competitive for technology roles and increases rapidly with experience.
Mid-level analysts with 2-3 years experience can expect ₹8-15 lakhs as they move into L2 roles with deeper investigative responsibilities.
Global opportunities (especially remote positions) start around $60,000+ annually for entry-level roles, with substantial growth potential.
Senior SOC roles, threat hunting positions, and SOC management can scale significantly higher as you progress.
The career trajectory is real. We’ve seen students go from complete beginners to L2 analysts within 18-24 months by combining training with consistent skill application.
Why Choose Go Hackers Cloud for SOC Analyst Training
Every training provider claims they’re the best. So why should you trust us?
Go Hackers Cloud focuses on outcomes, not just content delivery.
What actually sets us apart:
Real SOC lab environment that doesn’t disappear when your course ends. You’ll have extended access to practice, experiment, and build portfolio projects that demonstrate your skills to employers.
Industry-experienced mentors who’ve actually worked in SOC environments. They’ve investigated real incidents, dealt with real pressure, and made real mistakes they’ll help you avoid.
Job-focused curriculum designed backward from what employers actually need. We talked to hiring managers, reviewed job descriptions, and built training that addresses real skill gaps.
Interview preparation support including mock SOC interviews where you’ll answer technical questions, explain your investigative process, and demonstrate problem-solving approaches.
Resume and LinkedIn optimization because your skills mean nothing if recruiters can’t find you or understand your value from your profile.
We’re not satisfied with just teaching concepts. You need to practice, apply, and ultimately get hired. That’s our measure of success.
Placement Support & Career Mentorship
Training without placement support is incomplete.
Our SOC analyst training with placement support includes structured career development that continues beyond technical training.
What placement support actually means:
Mock SOC interviews that simulate real hiring scenarios. You’ll face technical questions about log analysis, incident response decisions, and tool usage. We’ll identify gaps and help you improve before real interviews.
Resume review by industry professionals who understand what SOC hiring managers look for. Your resume needs to highlight practical skills and project experience effectively.
Career mentorship sessions where you can discuss job search strategies, salary negotiations, company culture considerations, and career progression planning.
Job referrals and hiring guidance connecting you with companies actively recruiting SOC analysts. We maintain relationships with hiring managers who trust our training quality.
This support continues after training completion because job searching takes time and persistence. You’re not alone in that process.
How to Enroll in SOC Analyst Training
Getting started is straightforward.
Book a free career consultation where we’ll discuss your background, career goals, and how SOC analyst training fits your situation. This isn’t a sales pitch it’s a genuine conversation about whether this path makes sense for you.
Choose your learning mode based on your schedule and learning preferences. We offer flexibility because everyone’s situation is different.
Start hands-on SOC labs immediately. You won’t wait weeks before touching actual tools. Lab access begins early so you can start building practical experience.
Get certified and job-ready through structured progression that builds confidence alongside competence.
Our admissions team supports you throughout the enrollment process, answering questions and ensuring you’re set up for success from day one.
Ready to transform your career? Visit https://gohackerscloud.com/ and book your free consultation today. Join our community at Discord to connect with fellow learners and industry experts.
FAQs About SOC Analyst Training
Is SOC analyst training suitable for complete beginners?
Absolutely. Our SOC analyst training for beginners starts from foundational concepts and builds progressively. We don’t assume prior cybersecurity knowledge. If you’re willing to learn and practice consistently, you can succeed regardless of your starting point.
Do I need coding or programming skills?
No advanced coding is required. Basic scripting concepts are introduced gradually within the training context. Most SOC work involves understanding security concepts and using existing tools effectively rather than building new software.
Is this SOC analyst course online or in-person?
The SOC analyst course online format includes live sessions with instructors and on-demand lab access. You’ll interact with mentors and other learners while maintaining schedule flexibility.
What specific tools will I gain experience with?
You’ll work with SIEM platforms, endpoint detection tools, security orchestration systems, and threat intelligence platforms. The focus is on understanding tool categories and transferable skills rather than becoming dependent on one specific vendor.
Does Go Hackers Cloud provide actual placement support?
Yes. Placement support includes resume optimization, interview preparation, mock interviews, and connections to hiring companies. While we can’t guarantee job placement (no ethical provider can), we provide structured support that significantly improves your hiring prospects.
How long does the training take to complete?
Duration varies based on your pace and prior experience. Most learners complete the core curriculum within 3-6 months while balancing other commitments. Lab access extends beyond course duration for continued practice.
What’s the difference between this and watching free YouTube videos?
Structured curriculum, hands-on labs with real tools, mentor feedback, and career support. Free resources are great for exploration, but they don’t provide the guided practice and accountability that builds job-ready skills.
Can I work while taking this training?
Yes. The flexible learning format supports working professionals. Many of our successful students maintained full-time jobs while completing training.
Your SOC Analyst Career Starts Here
The cybersecurity skills gap isn’t closing anytime soon. Organizations need trained SOC analysts who can actually do the work, not just talk about concepts.
Go Hackers Cloud’s SOC analyst training gives you hands-on experience with real SIEM tools, practical incident response skills, and the career support that helps you land that first role.
We’re not promising overnight success or unrealistic outcomes. We’re offering structured training, experienced mentorship, and genuine support for people serious about breaking into cybersecurity.
Hundreds of students have already made the transition. Some started as complete beginners. Others came from unrelated IT fields. What they shared was commitment to learning and willingness to practice consistently.
The question isn’t whether SOC analyst roles are in demand. They absolutely are.
The question is whether you’re ready to invest in training that actually prepares you for those roles.
If you’re tired of surface-level courses that leave you unprepared for real work, if you want hands-on experience with tools that matter, if you need career support that extends beyond content delivery then you’re in the right place.
Transform your career with job-focused SOC analyst training. Real labs. Real tools. Real career support.
Visit https://gohackerscloud.com/ now and book your free career consultation. Join our Discord community at Discord to connect with current students, alumni, and cybersecurity professionals. Let’s discuss your cybersecurity future.


