Cybersecurity isn’t about reading slides anymore. It’s about jumping into live threats, analyzing messy logs at 2 AM, and making split-second decisions that protect entire organizations. That’s the reality of SOC work.
And honestly? Most training programs miss this completely.
We’ve seen too many aspiring analysts finish courses only to freeze during their first real alert. They know the theory. They’ve memorized acronyms. But when faced with actual malicious traffic or a potential breach, they don’t know where to start.
That changes with SOC analyst training with hands-on labs.
At Go Hackers Cloud, we’re not interested in creating certificate collectors. We’re building analysts who can walk into a SOC on day one and actually contribute. Real tools. Real attacks. Real pressure.
Let’s break down exactly what that means for your career.
Why Hands-On Labs Matter in SOC Analyst Training
Here’s something most people don’t tell you: SOC analyst practical training separates those who get hired from those who stay stuck in the application cycle.
Recruiters can spot theoretical knowledge instantly. They’ve seen hundreds of resumes listing “familiar with SIEM” or “understands incident response.” But when they ask, “Walk me through how you’d investigate a brute force attack,” that’s where most candidates stumble.
Because knowing about something and actually doing it are completely different skills.
With SOC analyst training with hands-on labs, you’re not watching demonstrations. You’re the one:
- Triaging alerts that flood in during simulated attacks
- Writing queries to hunt suspicious activity across thousands of logs
- Documenting incidents under time constraints
- Making containment decisions when malware spreads
This muscle memory doesn’t come from videos. It comes from repetition in environments that mirror real SOC chaos.
We’ve watched students transform after their first few lab sessions. The uncertainty fades. The confidence builds. And suddenly, they’re speaking the language that hiring managers want to hear.

Real-World SOC Environment Explained
Walk into any enterprise SOC and you’ll see the same thing: organized chaos.
Multiple screens. Constant alerts. Analysts juggling investigations while new incidents queue up. It’s nothing like the clean, step-by-step scenarios you see in sanitized demos.
Our SOC analyst real-world training replicates this environment deliberately.
You won’t work in simplified sandbox playgrounds. Instead, you’ll navigate:
- Multi-tier alert workflows where Tier 1 passes complex cases to Tier 2
- Noisy environments with both legitimate activity and actual threats mixed together
- Ticketing systems requiring proper documentation and chain of custody
- Escalation procedures mimicking real SOC hierarchies
One student told us their biggest surprise wasn’t the technical difficulty. It was learning to prioritize when five critical alerts hit simultaneously. That’s the kind of decision-making traditional courses never teach.
Because in SOC analyst lab-based course training at Go Hackers Cloud, we don’t give you one alert to analyze for an hour. We give you twenty alerts to triage in fifteen minutes. Just like the real job.
Want to explore the complete curriculum? Check out our comprehensive SOC analyst training program designed for real-world readiness.
Tools Used in SOC Analyst Hands-On Labs
Let’s be direct: if you can’t work SIEM tools, you can’t work in a SOC.
Period.
But “working SIEM” means more than clicking through a tutorial. It means understanding data normalization, building correlation rules, tuning alerts to reduce false positives, and extracting meaning from raw logs that look like gibberish to untrained eyes.
Our SOC analyst training with hands-on labs provides deep exposure to:
Core SIEM Platforms
You’ll spend serious time in Splunk and ELK Stack environments, learning both the interface and the underlying logic. Not surface-level demos actual query writing, dashboard creation, and alert configuration.
Endpoint Detection and Response (EDR) Tools
Modern SOCs don’t rely on SIEM alone. You’ll work with EDR platforms to track process execution, file modifications, and network connections at the endpoint level.
Threat Intelligence Platforms
Learning to enrich alerts with threat intel context turns you from someone who sees an IP address into someone who understands it’s linked to a known APT group.
Log Management Systems
Before analysis comes collection. You’ll configure log sources, understand parsing, and troubleshoot when critical logs stop flowing.
Incident Management Tools
SOC work requires documentation. You’ll use ticketing systems that track investigations from initial detection through final remediation.
Here’s what matters: you don’t just see these tools in screenshots. You configure them. Break them. Fix them. And learn their quirks through hours of actual use.
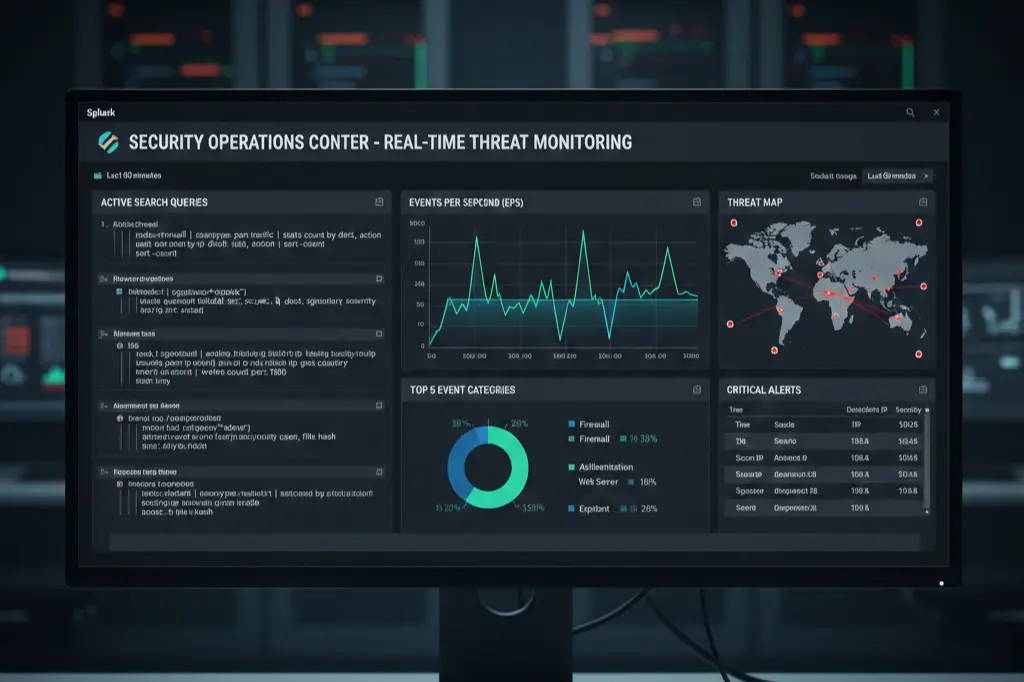
SIEM Use Cases and Log Analysis Practice
This is where theoretical knowledge dies and practical skills are born.
Understanding what SIEM does is easy. Actually using SIEM to find a sophisticated attacker hiding in millions of daily events? That’s a completely different challenge.
Through SOC analyst training with real-time labs, you’ll build and tune use cases for:
Authentication Anomalies
Failed logins happen constantly in enterprise environments. Your job is distinguishing between a locked-out employee and an attacker running password sprays. You’ll write correlation rules that detect patterns, not just individual events.
Lateral Movement Detection
Attackers rarely stay on their initial entry point. You’ll track suspicious SMB traffic, unusual service account behavior, and authentication patterns that suggest pivoting between systems.
Data Exfiltration Indicators
Large outbound transfers? Maybe. Or maybe it’s legitimate backup traffic. You’ll learn to correlate file access logs, network traffic, and user behavior to spot the difference.
Privilege Escalation
When standard users suddenly execute admin-level commands, your alerts should fire. But not every elevation is malicious. You’ll tune detection to catch real threats while avoiding alert fatigue.
This SOC analyst training using SIEM tools approach ensures you understand not just what an alert says, but why it triggered and what investigation steps come next.
One of our recent graduates shared that their first week on the job, they caught a compromised account that two senior analysts had missed. Not because they were smarter because they’d practiced this exact scenario in our labs dozens of times.
Ready to master SIEM like a professional SOC analyst? Start your hands-on journey at Go Hackers Cloud and gain skills that actually matter in SOC roles.
New to cybersecurity? Our SOC analyst training for beginners starts with fundamentals and builds to advanced skills.
Incident Detection and Response Labs
Detection gets the headlines. But response is where careers are built.
Anyone can see an alert fire. Knowing what to do next immediately, correctly, and under pressure separates entry-level analysts from those who advance quickly.
Our SOC analyst training with live incident response throws you into scenarios that SOC teams face weekly:
Ransomware Outbreak Simulations
You’ll work through the complete lifecycle: initial detection of suspicious file encryption, containment to prevent spread, forensic analysis to identify patient zero, and post-incident reporting.
Phishing-Turned-Compromise
Starting with a reported suspicious email, you’ll investigate whether the user clicked the link, what payload executed, what persistence mechanisms deployed, and whether lateral movement occurred. Just like real investigations unfold.
Insider Threat Scenarios
These are messy. Legitimate credentials. Expected system access. You’ll learn to spot behavioral anomalies and build evidence chains that distinguish malicious intent from policy violations.
Web Application Attacks
SQL injection attempts. Command injection. You’ll correlate web server logs, application logs, and database logs to understand attack vectors and assess damage.
Advanced Persistent Threat (APT) Campaigns
Multi-stage attacks spanning days or weeks. You’ll piece together disconnected events, identify C2 communication, and track attacker objectives.
Each lab follows the NIST incident response framework: Preparation, Detection, Analysis, Containment, Eradication, Recovery, and Lessons Learned.
Because this is how SOC analyst real-world training should work not simplified scenarios with obvious answers, but complex investigations requiring critical thinking.
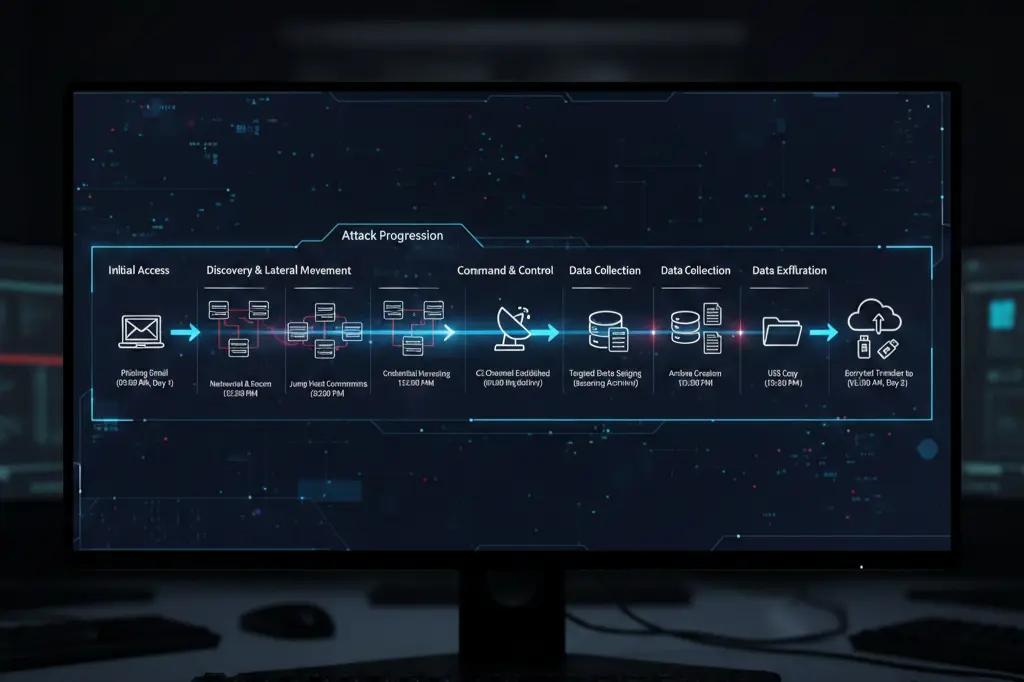
Threat Intelligence and Alert Triage Exercises
Here’s the uncomfortable truth about SOC work: you’ll face hundreds of alerts daily. Most are false positives. Some are misconfigurations. A few are real threats.
Your job? Figure out which is which. Fast.
This is where SOC analyst practical training becomes invaluable.
In our alert triage labs, you’ll work through realistic scenarios:
IP Reputation Analysis
An alert fires on outbound traffic to an unknown IP. Is it malicious? You’ll check threat intel feeds, passive DNS records, WHOIS data, and historical traffic patterns to make that call.
File Hash Investigation
An executable appears on a user’s system. VirusTotal shows mixed results. You’ll analyze file behavior, check sandbox detonation reports, and correlate with endpoint telemetry.
Domain Analysis
Newly registered domain? Typosquatting attempt? Legitimate service? You’ll use OSINT techniques and threat intelligence platforms to assess risk.
Alert Enrichment
Raw alerts lack context. You’ll practice adding user information, asset criticality, historical behavior, and threat intelligence to transform “unknown alert” into “actionable intelligence.”
False Positive Reduction
Not every alert deserves investigation. You’ll learn to tune rules, create exceptions, and improve signal-to-noise ratios without missing real threats.
Students consistently tell us this training changed how they think. Instead of panicking at alert volume, they develop systematic triage workflows that prioritize actual risk.
Go Hackers Cloud embeds threat intelligence practice throughout the curriculum because real SOC analysts don’t just react they contextualize.
Looking for lab-intensive learning? Discover our practical SOC analyst training that emphasizes real-world scenarios over theory.
Blue Team Attack Simulation Scenarios
This is where everything comes together.
Most courses teach you to investigate attacks that already happened. We go further: you’ll defend against attacks as they unfold.
Our SOC analyst training with hands-on labs includes blue team simulations where:
Red Team Attacks Generate Real Alerts
Simulated attackers execute real techniques phishing, exploitation, privilege escalation, lateral movement. Your SIEM generates genuine alerts based on their actions.
You Investigate in Real-Time
No prepared walkthroughs. No “here’s what to look for” hints. You see the same alerts real analysts see and must determine severity, investigate scope, and recommend response.
You Make Containment Decisions
Do you isolate the affected system? Block the IP? Disable the account? Each decision has consequences, and you’ll learn to balance thoroughness with speed.
You Document Like It Matters
Because in real SOCs, documentation is everything. You’ll write incident reports, create timelines, and present findings skills that employers specifically ask about.
One graduate described their first blue team exercise as “controlled panic.” They knew the theory. But when alerts started firing and they had to coordinate response while attackers adapted? That tested everything.
By the fifth simulation, they moved with confidence. They knew their tools. They trusted their process. They made decisions.
That transformation doesn’t happen in lecture halls. It happens in SOC analyst lab-based course environments that mirror real pressure.

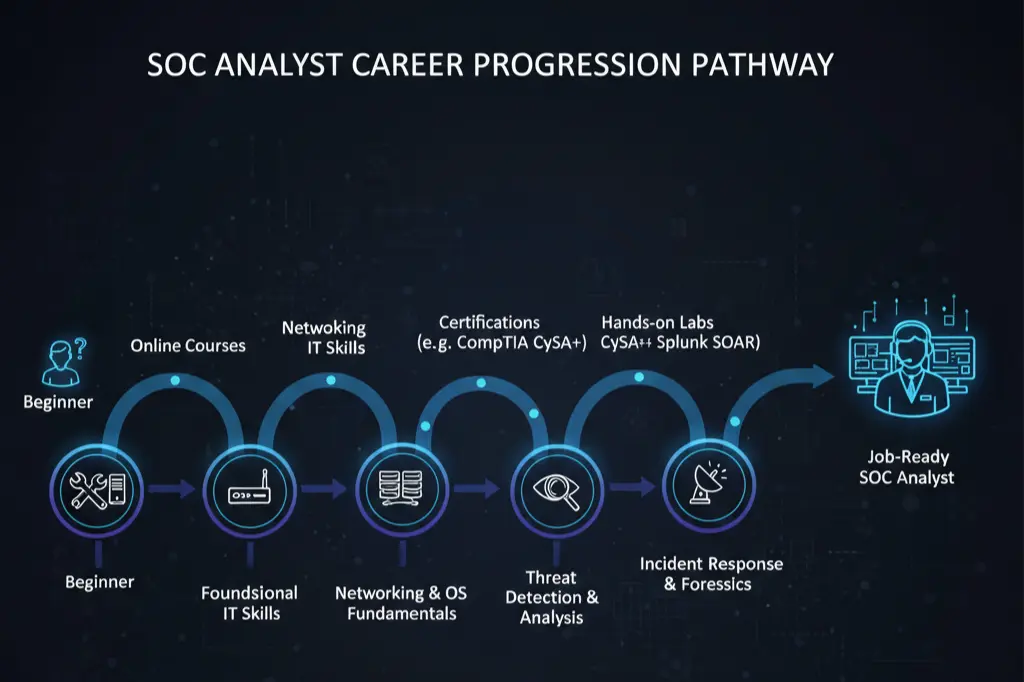
How Hands-On Training Improves Job Readiness
Let’s talk about what happens after training.
You’ll submit resumes. You’ll interview. And at some point, someone will ask: “Can you actually do this job?”
With SOC analyst training with hands-on labs, your answer changes.
Instead of: “I completed a course on incident response,” you say: “I’ve investigated over fifty simulated incidents, including ransomware, APTs, and insider threats. I’m comfortable with Splunk, EDR tools, and threat intelligence platforms. I can walk you through how I’d approach any scenario you describe.”
That confidence comes from repetition. From making mistakes in labs where the stakes are low. From refining your approach until investigation workflows become second nature.
Employers Notice Practical Experience
We’ve placed students who competed against candidates with longer resumes and more certifications. The difference? Our students could discuss specific investigations, explain their decision-making process, and demonstrate tool proficiency.
Interview Performance Improves Dramatically
When asked behavioral questions, you won’t reach for theoretical examples. You’ll reference specific labs: “In one simulation, I detected lateral movement by correlating failed RDP attempts with successful SMB authentication. Here’s how I approached that investigation.”
Onboarding Time Decreases
New SOC analysts typically spend weeks just learning tools and workflows. You’ll walk in already familiar with SIEM interfaces, ticketing systems, and investigation methodologies.
Career Progression Accelerates
Entry-level roles become stepping stones, not destinations. The practical foundation lets you absorb new concepts faster and contribute beyond basic alert monitoring.
This is why Go Hackers Cloud builds courses around capabilities, not just curriculum. We care about what you can do, not just what you’ve seen.
Why Go Hackers Cloud Labs Stand Out
Every platform claims hands-on training now. The term has lost meaning.
So let’s be specific about what makes Go Hackers Cloud different:
Industry-Aligned Lab Environments
Our labs aren’t built by instructional designers who’ve never worked SOC shifts. They’re designed by professionals who’ve lived through alert storms, incident escalations, and 3 AM emergency responses. The scenarios reflect real operational challenges.
Continuous Lab Access
Learning doesn’t happen in scheduled three-hour blocks. You need to practice when concepts click, which might be 11 PM on a Tuesday. Our lab environments stay available so you can build skills on your schedule.
Mentor-Guided Investigations
Stuck on a complex investigation? Our mentors have worked through similar cases in production environments. They don’t just give answers they guide you through the thinking process real analysts use.
Progressive Difficulty Scaling
Early labs build foundational skills with clear objectives. Advanced simulations introduce ambiguity, time pressure, and incomplete information just like real incidents.
Tool Diversity
We don’t lock you into one vendor’s ecosystem. You’ll work with multiple SIEM platforms, various EDR tools, and different log sources because real careers require adaptability.
Real Attack Techniques
Our red team simulations use current MITRE ATT&CK techniques. You’re defending against the same methods attackers use today, not outdated scenarios from five years ago.
Students frequently tell us they didn’t realize how much they’d learned until interviews. They’d internalized workflows, developed intuition, and built confidence through repetition.
That’s not accident. That’s intentional design from a team that understands SOC analyst training with hands-on labs needs to prepare you for real work, not just exams.
Want to experience the difference? Explore comprehensive SOC analyst training with hands-on labs at Go Hackers Cloud and see why practical experience matters.
Enroll in SOC Analyst Hands-On Training
Theory creates awareness. Labs create capability.
If you’re serious about becoming a job-ready SOC analyst, you need more than lectures and multiple-choice quizzes. You need environments where mistakes teach lessons. Where investigations build muscle memory. Where tools become extensions of your thinking rather than obstacles to overcome.
At Go Hackers Cloud, we’ve built SOC analyst training with hands-on labs specifically for people who want to work in cybersecurity, not just learn about it.
Real SIEM platforms. Real attack scenarios. Real investigation workflows. Real career outcomes.
The gap between training completion and job competency shouldn’t exist. With proper practical preparation, you can walk into SOC roles ready to contribute from week one.
That’s what we deliver. Not promises. Results.
Frequently Asked Questions
Is this SOC analyst training suitable for complete beginners?
Absolutely. We’ve designed the program for career switchers and beginners. The curriculum starts with fundamentals what a SOC does, basic networking concepts, security principles then progressively builds to advanced investigation techniques. You don’t need prior cybersecurity experience. You need curiosity and commitment.
What if I have no IT background at all?
Basic computer literacy is helpful, but extensive IT experience isn’t required. Many successful students came from non-technical backgrounds. We’ve included foundational modules that establish necessary context before diving into SOC-specific skills.
Which specific SIEM tools will I learn?
You’ll gain substantial hands-on experience with Splunk and ELK Stack environments. The focus isn’t just clicking buttons you’ll understand query languages, correlation logic, alert tuning, and dashboard creation. These skills transfer across SIEM platforms because you’re learning the underlying concepts, not just vendor-specific interfaces.
How much time should I expect to spend in labs weekly?
Most students spend eight to twelve hours weekly in lab environments, though access remains available whenever you want to practice. The key is consistent engagement rather than cramming. Regular practice builds the pattern recognition and muscle memory that makes real SOC work manageable.
Do you provide job placement assistance after training?
Yes. Go Hackers Cloud offers comprehensive career support including resume optimization for SOC roles, interview preparation with actual hiring manager questions, portfolio development showcasing your lab work, and guidance on job search strategies. We’re invested in your career outcomes, not just course completion.
Will I receive a certificate?
You’ll receive a certificate documenting your training completion and skills acquired. But more importantly, you’ll have a portfolio of investigations, SIEM queries, incident reports, and lab outcomes that demonstrate practical capability to employers.
How current is the training content?
We continuously update labs to reflect current attack techniques and industry practices. Our simulations incorporate MITRE ATT&CK framework methods, ensuring you’re prepared for threats organizations face today, not outdated scenarios.
Can I access labs after completing the course?
Yes. Extended lab access continues beyond formal training completion, allowing you to refresh skills, practice before interviews, or explore advanced scenarios as your career develops.
Transform Your Career with Real SOC Skills
Most people approach cybersecurity training backwards. They collect certificates hoping doors will open. They memorize facts expecting competence will follow.
But SOC work doesn’t reward theoretical knowledge. It rewards practical capability.
The ability to look at overwhelming log data and spot the one suspicious pattern. The confidence to investigate complex alerts without second-guessing every step. The experience to make sound decisions under pressure.
That only comes from doing the work. Repeatedly. In environments that simulate real operational challenges.
Go Hackers Cloud built SOC analyst training with hands-on labs for people who understand this reality. For people ready to invest time in developing actual skills rather than just adding credentials to LinkedIn.
If that describes you if you’re committed to becoming genuinely job-ready rather than just training-complete we should talk.
Your SOC career doesn’t start with your first job. It starts the moment you begin investigating your first simulated incident, writing your first SIEM query, making your first containment decision.
Start that journey now. Enroll in SOC Analyst Training with Real Hands-On Labs at Go Hackers Cloud and build the practical skills that SOC roles demand.
Join our vibrant community of aspiring SOC analysts, get mentorship, and stay updated with the latest cybersecurity trends. Connect with us on Discord and start networking with fellow learners and industry professionals.
Your future colleagues are already in the labs. Join them.


